Unlocking the Power of Zero Trust Networks
Cybersecurity is more crucial than ever in today’s rapidly evolving digital landscape. Traditional perimeter-based security models have proven inadequate as cyber threats grow in sophistication. This is where Zero Trust Networks come into play—a modern approach to security that offers resilience and flexibility. For cybersecurity professionals, executive leaders, and IT managers, understanding and implementing Zero Trust can significantly bolster your organization’s defenses.
What is Zero Trust?
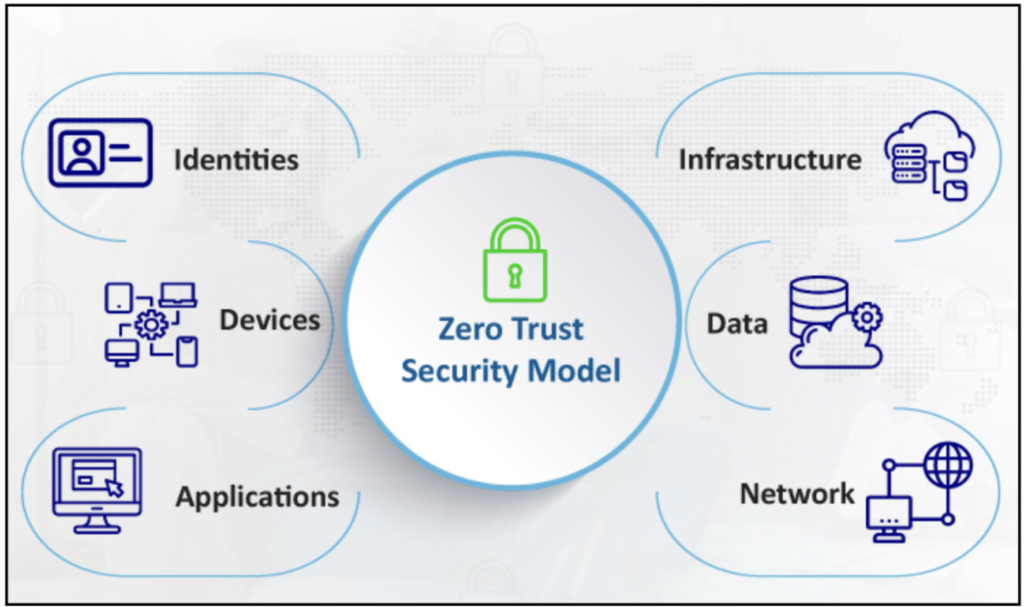
Zero Trust is a security framework that requires all users, even those inside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted access to applications and data. It operates on the principle of “never trust, always verify.” This approach protects sensitive data and mitigates risks associated with unauthorized access.
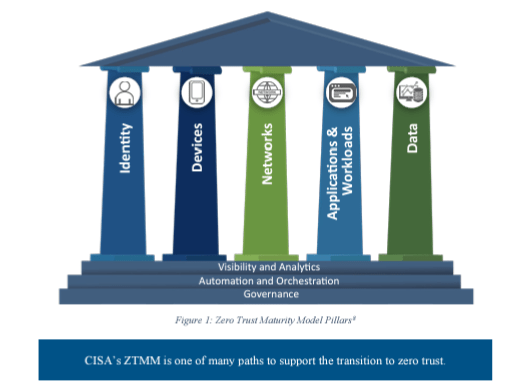
America’s Zero Trust Maturity Model Provides an Ungated 40+ page Explanation of the Zero Trust Journey.
Click here for a downloadable version of the Zero Trust Maturity Model V2.0.
Why Traditional Security Models Fall Short
Traditional security models rely heavily on perimeter defenses—such as firewalls, VPNs, and intrusion detection systems—to protect the network by creating a digital barrier between internal systems and external threats. While these measures are essential, they often prove insufficient in today’s cloud-based and remote-working environments. As organizations adopt cloud services and support remote work, their attack surface increases, and perimeter defenses alone can no longer provide adequate protection.
Limitations of Perimeter-Based Security
Lateral Movement of Attackers
Once an attacker breaches the perimeter, they can move laterally across the network, exploiting vulnerabilities and gaining access to critical systems without being detected. This is especially dangerous because traditional security measures often lack the ability to monitor internal movements effectively.
Example: In the case of the 2014 Sony Pictures breach, attackers entered through a compromised workstation and moved laterally across the network, gaining access to sensitive financial data and unreleased films. The lack of internal segmentation allowed the attackers to escalate their privileges and maintain access for an extended period without detection.
Insider Threats
Perimeter defenses focus on external threats but offer limited protection against malicious insiders or compromised internal accounts. If an employee’s credentials are stolen, the attacker can gain unrestricted access to internal systems through VPNs or other trusted access points.
Example: In 2019, a malicious insider at Capital One accessed sensitive customer data, including Social Security numbers and credit card applications. Because the attacker had insider access, traditional perimeter defenses were bypassed, and the incident was only discovered through external reporting.
Cloud Adoption and Remote Work Challenges
As organizations adopt cloud-based services and support remote employees, the concept of a fixed network perimeter dissolves. Traditional perimeter defenses struggle to secure distributed environments, where users, devices, and applications reside both inside and outside the organization’s network. VPNs and firewalls can create bottlenecks, limiting flexibility and increasing latency for remote workers.
Example: During the COVID-19 pandemic, many companies faced challenges as their employees moved to remote work environments. Cybercriminals took advantage of unsecured home networks to launch phishing and ransomware attacks, bypassing traditional defenses that relied on in-office setups and firewall protections.
Supply Chain Attacks
Traditional security models assume that partners, suppliers, and third-party vendors are trusted. However, modern supply chain attacks target vulnerabilities in third-party software, hardware, or services, allowing attackers to bypass perimeter defenses and gain access to internal systems.
Example: The SolarWinds attack in 2020 demonstrated the inadequacy of perimeter security. Attackers inserted malicious code into a software update, which was downloaded by several government agencies and private companies. The compromised software gave attackers privileged access to internal networks, remaining undetected for months.
How Zero Trust Addresses These Shortcomings
Zero Trust overcomes these vulnerabilities by assuming that threats could come from both external and internal sources. It enforces strict identity verification for all users and devices, continuously monitors access, and limits privileges based on roles. This model prevents attackers from moving laterally within the network, mitigates risks from insider threats, and ensures that cloud and remote work environments remain secure. Additionally, it enables organizations to validate third-party access continuously, reducing exposure to supply chain attacks.
The Cloud Security Alliance Provides Dozens of Ungated Resources Concerning How to Implement a Zero Trust Network – We highly recommend the site cloudsecurityalliance.org.
Core Components of a Zero Trust Network
- Strict Identity Verification: Requires comprehensive authentication and authorization for users and devices.
- Least Privilege Access: Limits user access to only what is necessary for their role, reducing potential exposure of sensitive information.
- Microsegmentation: Divides the network into isolated segments, each protected individually to contain breaches.
- Real-Time Threat Detection: Continuously monitors network activity to identify anomalies and potential threats promptly.
The Benefits of Zero Trust
Enhanced Data Protection
Zero Trust significantly reduces the risk of data breaches by ensuring that only authenticated and authorized personnel can access sensitive information. Combined with microsegmentation, this approach creates robust defenses that protect against unauthorized access and internal misuse.
Example: A healthcare organization with patient data in multiple systems can prevent unauthorized access to Protected Health Information (PHI) by limiting access only to doctors and administrators. Even if an attacker breaches one part of the system, microsegmentation ensures they cannot access other critical systems, such as the billing or HR databases.
Increased Visibility and Control
Zero Trust policies provide complete visibility into all user activities, network traffic, and system interactions. This oversight helps organizations identify potential security gaps, detect unusual behaviors, and prevent lateral movement across the network.
Example: A financial institution uses Zero Trust to monitor all network traffic for anomalies, such as an employee accessing data outside their usual work hours. An alert triggers a security review, allowing the team to mitigate the threat before sensitive financial data is compromised.
Minimized Attack Surface
With Zero Trust, the network is segmented into isolated zones, and access is denied by default unless users and devices are fully verified. This reduces the organization’s attack surface, making it harder for attackers to gain access to critical systems.
Example: A manufacturing company utilizing connected IoT devices implements microsegmentation to isolate each device from others. If one device becomes compromised, such as through ransomware, the rest of the network remains unaffected, preventing widespread disruption.
Agility and Scalability
Contrary to popular belief, Zero Trust enhances organizational agility by enabling secure access from any location. It supports the remote workforce and allows seamless deployment of new applications without compromising security.
Example: A technology company allows its developers to access the system remotely while maintaining strict access policies through Zero Trust. As a result, developers can securely push updates to production servers from any location, improving productivity while maintaining data security.
Compliance and Regulatory Alignment
Zero Trust simplifies compliance by implementing granular access controls and continuous monitoring. This ensures the organization meets industry-specific regulations and audit requirements, providing peace of mind to both clients and stakeholders.
Example: A healthcare provider operating under HIPAA regulations uses Zero Trust to restrict access to medical records, ensuring compliance with data protection standards. Continuous monitoring also makes it easier to generate detailed reports for audits, reducing the time and effort required for regulatory reviews.
Implementing Zero Trust in Your Organization
To unlock the full potential of Zero Trust, organizations must start by identifying sensitive data and mapping out who has access to it. Limiting access, monitoring all data-related activities, and establishing a baseline of network activity are crucial steps. Utilizing analytics tools will further enhance threat detection and response capabilities.
Conclusion
Zero Trust Networks offer a paradigm shift in cybersecurity, focusing on identity verification, least privilege access, and continuous monitoring to secure sensitive data effectively. By adopting Zero Trust practices, organizations can strengthen their cybersecurity posture, ensuring greater protection against evolving threats.
For further details on how to implement Zero-Trust or if you’ve experienced a security breach, our team is here to assist. Call us at 1 (858) 349-2610 or fill out our Contact Us Form to speak with a security specialist. Together, we can ensure your organization’s cybersecurity defenses are robust and future-ready.