Modernizing & Streamlining SOC Operations to Thwart Attacks – Part 2
In Modernizing and Streaming SOC Operations, we discussed getting full visibility of your infrastructure and boosting your detection capabilities. In part 2, we will discuss tuning your security technology to reduce alert noise and uncover threats, automate your SOC where you can, and specifically, incident response automation. So, let’s get to it.
Fine-Tune Your Custom Rules
Custom alert rules are the backbone of effective threat detection but must be tailored to your organization’s specific threats. If you’re using generic rules or a “one-size-fits-all” approach, you’ll miss critical threats or be overwhelmed with irrelevant alerts. Here’s how to fine-tune your custom rules to make sure they’re doing their job:
- Relevance: Start by understanding your organization’s unique threat landscape. Look at your industry, the technologies you use, and common attack vectors you’ve seen in the past. This helps you create rules that focus on detecting the threats most likely to target your environment. For example, rules that focus on detecting phishing attacks targeting patient data or ransomware threats would be crucial if you operate in the healthcare sector.
- Accuracy: False positives are one of the biggest challenges in SOC operations. If your alert rules are too broad, they’ll trigger too many alerts for benign activities, which will exhaust your team and make it easy to miss genuine threats. Regularly refine your rules by adjusting them based on historical data and feedback from your analysts. SIEM tools like ArcSight and Microsoft Sentinel can provide analytics that helps you tweak your rules over time by analyzing past incidents and the patterns they exhibit.
- Prioritization: Not all alerts are created equal. Your rules should categorize alerts by critical, high, medium, and low severity. This way, your SOC team can focus on the most dangerous threats first and not waste time on lower-priority issues. You can create rules that trigger critical alerts when key assets (like sensitive databases) are targeted, while less risky activities could trigger lower-priority alerts.
- MITRE ATT&CK Framework: Using frameworks like MITRE ATT&CK as a guide when developing your custom rules ensures you have comprehensive coverage of all potential attack vectors. The framework outlines common tactics, techniques, and procedures (TTPs) that attackers use, allowing you to map your detection rules to each phase of an attack lifecycle.
- Testing and Tuning: Rules should be continuously tested and updated based on incident response data. Security Orchestration, Automation, and Response (SOAR) platforms like Palo Alto Cortex XSOAR allow you to automate the tuning process by feeding in data from past incidents and dynamically adjusting the rules. By automating these updates, you can ensure your rules remain accurate and effective without requiring constant manual adjustments.
Tools like Splunk or IBM QRadar allow you to build rules based on threat intelligence feeds specific to your industry or region. This ensures that your SOC isn’t bogged down by irrelevant alerts.
Also, leveraging machine learning in tools like Darktrace or Cortex XDR can reduce false positives by learning the expected behavior of your environment. These tools automatically adjust detection rules based on real-time behavior analysis, fine-tuning them without manual intervention.
Cisco Stealthwatch and CrowdStrike Falcon help with this by providing threat scoring, which automatically ranks detected threats based on their potential risk. This allows SOC teams to prioritize response efforts, starting with the highest severity incidents.
For example, MITRE ATT&CK can help you set up rules for detecting initial access techniques (like phishing or exploiting public-facing applications) and post-compromise techniques (like lateral movement or privilege escalation). Tools like Splunk, QRadar, and SentinelOne integrate MITRE ATT&CK mappings into their dashboards, making it easier to visualize where your detection gaps may lie and adjust your custom rules accordingly.
Example: If you’re receiving a large number of alerts from phishing attempts, refining your alert rules to detect spear-phishing (which typically targets specific high-value individuals) rather than broad-based attacks will reduce noise. By incorporating threat intelligence feeds, such as those provided by Recorded Future or ThreatConnect, you can enrich your detection rules with the latest information about the specific attack vectors targeting your industry.
By regularly reviewing and fine-tuning your custom alert rules, your SOC can dramatically improve its efficiency. It can focus on real threats while reducing the noise from irrelevant or low-risk events.
Automate Where You Can
Automation is a game changer for modern SOCs, allowing them to scale up, reduce response times, and handle more incidents with fewer resources. By introducing AI and automation into your SOC, you can take repetitive, time-consuming tasks off your analysts’ hands and shift their focus to more critical issues. Here’s how to enhance automation in your SOC:
- Machine Learning: Machine learning can significantly improve threat detection by identifying suspicious patterns that traditional rule-based systems might miss. For example, tools like Darktrace or Vectra AI use machine learning to analyze network traffic and user behavior in real time, continuously learning what “normal” looks like for your environment. When deviations from the norm occur, these systems flag the activity as potentially malicious. This process reduces false positives and automates the detection of novel threats, enabling your SOC to focus on investigating actual risks.
- SOAR (Security Orchestration, Automation, and Response): SOAR platforms take automation to the next level by orchestrating entire workflows, from detection to response. By integrating various security tools (SIEM, EDR, NDR, threat intelligence feeds), SOAR platforms like Palo Alto Networks Cortex XSOAR, IBM Resilient, and Splunk Phantom can automate the incident response process. Here’s how it works:
- Automated Playbooks: With SOAR, you can create playbooks for common incidents (e.g., phishing, malware, or insider threats). Once a trigger event occurs, such as an alert from your SIEM, the playbook kicks in, executing pre-defined actions like isolating compromised devices, gathering forensic data, or even containing the threat automatically.
- Runbooks for Triage and Containment: Runbooks guide the SOC team step by step through more complex incidents, offering automated suggestions based on past cases. For example, Cortex XSOAR integrates with CrowdStrike Falcon to automatically pull endpoint data and launch automated triage processes, so your team doesn’t have to manually investigate every alert.
- Automated Investigations: Many SOAR platforms also provide pre-configured integrations with threat intelligence services (like Recorded Future or Anomali) to enrich alerts with context automatically. For example, if a malware alert is triggered, the SOAR platform can automatically query external threat intelligence databases to check if this malware has been seen before and what response actions are recommended.
Machine learning can also automate threat classification and prioritization. Splunk’s machine learning toolkit, for instance, uses historical data to improve alerting and threat prioritization accuracy, helping your SOC quickly identify the most pressing issues.
Incident Response Automation
- Automating incident response tasks helps your SOC handle a higher volume of incidents while maintaining fast reaction times. Fortinet’s FortiSOAR platform integrates with its entire suite of security tools to automate everything from initial alerting to threat remediation. The system can automatically block IP addresses, isolate infected endpoints, or trigger network segmentation based on the severity of the threat. CrowdStrike does something similar with its Falcon Insight XDR, automating responses like quarantining compromised devices, forcing password resets, and alerting key stakeholders in real time.
- Automation also enhances vulnerability management. Tools like Tenable.io or Rapid7 InsightVM automate vulnerability scans and patch management, ensuring that security gaps are identified and closed quickly, without human intervention.
- Case Management & Centralized Data: By integrating SOAR with case management platforms like ServiceNow, your SOC can also automate the process of tracking incidents from detection through resolution. Splunk Phantom, for instance, offers built-in case management to document every action taken on an alert, including automated remediation steps. This accelerates the process and ensures that no critical steps are missed.
- Automating Phishing Defense: Phishing attacks are some of the most common threats SOCs face, and automation can help dramatically improve response times. Platforms like Proofpoint or Mimecast have built-in capabilities to detect and quarantine phishing emails automatically. When a phishing email is identified, the system can automatically block it, remove it from all users’ inboxes, and generate alerts for the SOC team. Tools like Cortex XSOAR or Splunk Phantom can also automate the entire investigation by pulling URLs, attachments, and IOCs (indicators of compromise) from suspicious emails and cross-referencing them with threat intelligence feeds.
- Automated Threat Hunting: Automation isn’t just for responding to threats—it’s also for finding them. SOCs can leverage user and entity behavior analytics (UEBA) platforms like Exabeam or Microsoft Defender for Identity to continuously monitor for abnormal activities within their network. These tools apply machine learning to detect insider threats, compromised accounts, and other hard-to-spot malicious activities by automatically flagging suspicious behavior based on anomalies in user patterns.
Example: Companies like Palo Alto Networks and CrowdStrike have deeply integrated automation into their SOC operations. For instance, CrowdStrike Falcon automatically triggers remediation workflows based on predefined policies, isolating compromised endpoints within seconds of detecting malicious activity. Palo Alto’s Cortex XSOAR integrates across cloud, network, and endpoint security solutions to automate even the most complex response scenarios, significantly reducing the time between detection and containment.
By embracing automation in your SOC, you can scale your operations and dramatically reduce response times, streamline workflows, and handle a larger volume of incidents with fewer resources.
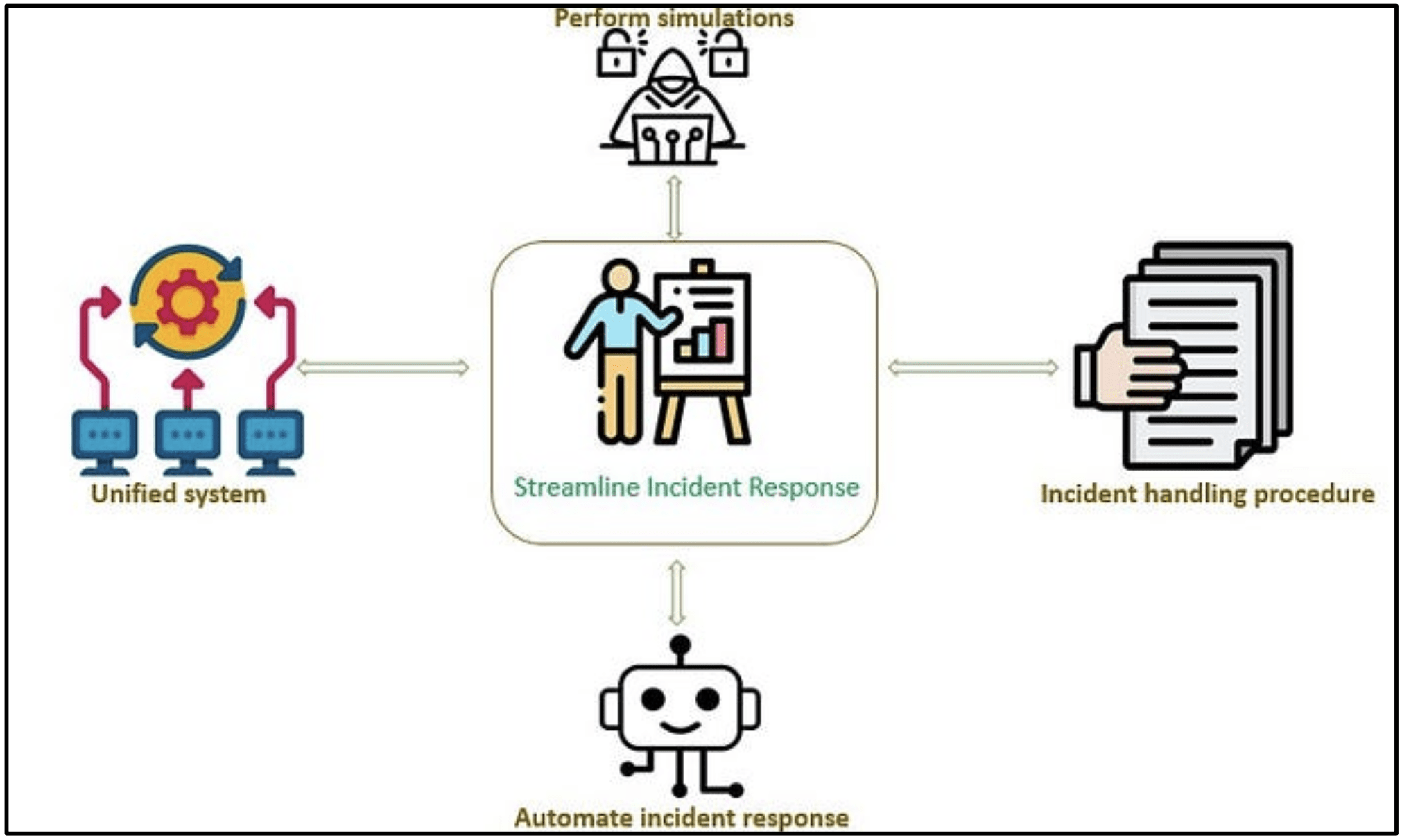
Summary on Streamlining Your Incident Response
An effective incident response plan is key to dealing with threats quickly and efficiently. But how can you improve it?
- Clear procedures: Establish a straightforward incident-handling process with clear escalation protocols.
- Simulations: Run attack simulations to test your team’s readiness. These drills help you spot gaps and improve response times.
- Unified alert systems: Centralize all your alerts into one system so your team doesn’t waste time juggling between tools.
For example, Splunk or Microsoft Sentinel offers centralized systems that track incidents from start to finish.
Summary of Key Security Solutions to Consider
Here’s a quick rundown of the essential tools to elevate your SOC:
- SIEM Solutions – Real-time analysis of security alerts from different sources.
- Top vendors: Splunk, IBM QRadar, Microsoft Sentinel.
- EDR Solutions – Advanced endpoint security and continuous monitoring.
- Top vendors: CrowdStrike Falcon, Sophos, Microsoft Defender.
- Next-Gen Firewalls (NGFWs) – Beyond traditional firewalls, offering deep packet inspection and more.
- Top vendors: Palo Alto Networks, Fortinet, Cisco Firepower.
- Email Security – Blocking phishing attacks before they hit your inbox.
- Top vendors: Proofpoint, Mimecast, Cisco Email Security.
- Vulnerability Management – Identifying and patching security gaps.
- Top vendors: Tenable, Qualys, Rapid7.
Conclusion
A well-functioning SOC is your organization’s best defense against cyber threats. By focusing on these key areas—visibility, detection, automation, and response—you’ll ensure that your SOC operates like a well-oiled machine. Ensure you have the right tools, regularly refine your processes, and keep an eye on the latest security trends to stay ahead of attackers.
“A top-notch SOC isn’t just about the tools you use. It’s about how your technology and team work together to protect what matters most.”

