Modernizing & Streamlining SOC Operations to Thwart Attacks – Part 1
Running a Security Operations Center (SOC) is a big deal in today’s cybersecurity landscape. Your SOC acts as the nerve center for detecting and responding to cyber threats. But if your SOC isn’t up to speed, your organization could be vulnerable to data breaches and attacks. Don’t worry, though—there are simple ways to tighten things up.
Let’s break down a few key strategies to help your SOC run more smoothly and keep those cybercriminals at bay.
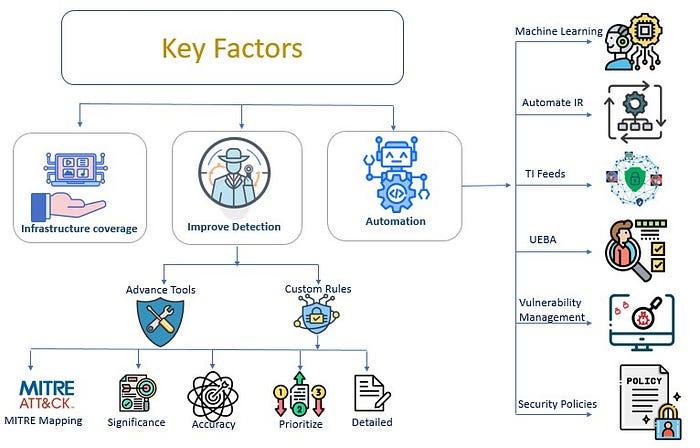
Get Full Visibility on Your Infrastructure
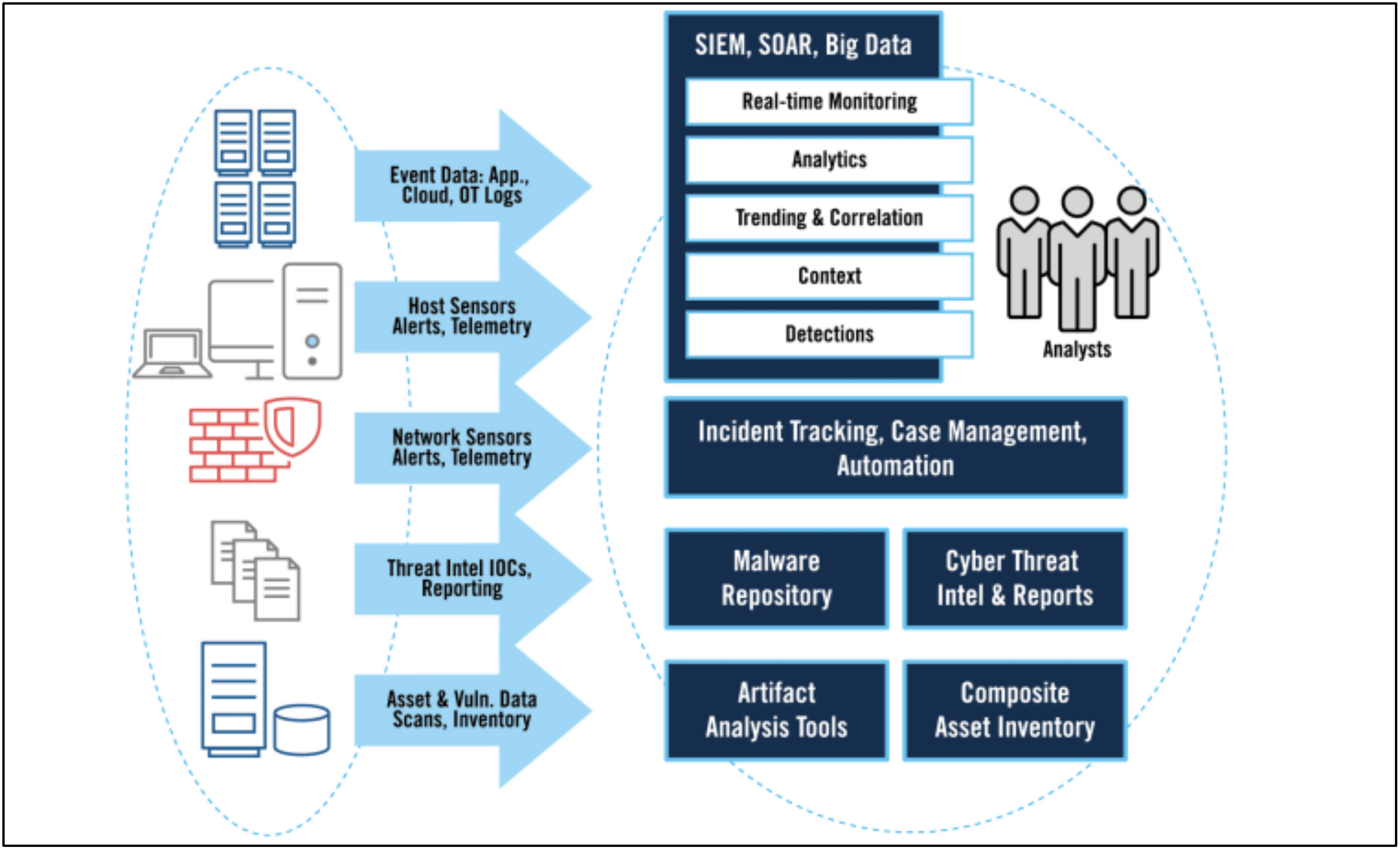
First things first—your SOC needs to see everything. Having full visibility means you’re keeping an eye on all critical parts of your infrastructure: networks, endpoints, servers, applications, and cloud services. But it’s not enough just to have separate tools monitoring each of these areas. You need a unified view that integrates all these systems, giving you a comprehensive picture of your organization’s security posture.
SIEM (Security Information and Event Management) tools, like Splunk Enterprise Security, IBM QRadar, and Microsoft Sentinel, offer this kind of integration. These tools aggregate logs and data from various sources across your infrastructure—whether it’s cloud platforms, firewalls, or endpoints—and analyze them in real-time. This way, your SOC can identify potential threats that might otherwise go unnoticed.
For example, Splunk pulls data from different systems and visualizes it, making it easier for your team to spot unusual patterns. It collects data from cloud services, network devices, and endpoint solutions, giving your SOC the eyes to see across every layer of your infrastructure.
Then there’s Microsoft Sentinel, which is designed for hybrid environments. It ties into Azure, on-premise solutions, and third-party services, offering advanced analytics to detect hidden threats and suspicious activities. Its AI-driven insights and automated threat responses streamline the entire monitoring process.
In addition to SIEM tools, EDR (Endpoint Detection and Response) solutions like CrowdStrike Falcon and VMware Carbon Black offer visibility at the device level. These tools continuously monitor endpoints for suspicious activities, alerting the SOC about any abnormal behaviors. For instance, CrowdStrike Falcon provides continuous visibility into endpoint activities while leveraging threat intelligence to assess the severity of threats in real-time.
NDR (Network Detection and Response) solutions, like Darktrace and Cisco Stealthwatch, focus on network traffic and spot anomalies and potential threats. Darktrace, for instance, uses AI to learn what ‘normal’ looks like for your network, which allows it to flag suspicious activity, even if it doesn’t match known threat signatures.
By combining these tools—SIEM for overarching insights, EDR for endpoint-specific data, and NDR for network activity—you can achieve full visibility across your infrastructure. This unified approach lets your SOC detect, respond, and mitigate threats more efficiently, ensuring the protection of all organizational assets.
Boost Your Detection Capabilities
Let’s be honest—traditional security tools don’t cut it anymore. Attackers are constantly evolving, and outdated defenses can’t keep up. Your SOC needs advanced threat detection tools that offer comprehensive and proactive monitoring to stay ahead. Here’s a breakdown of some go-to options and how they strengthen threat detection:
- SIEM (Security Information and Event Management): SIEM tools are the backbone of threat detection in many SOCs. They aggregate and analyze logs from various sources (servers, networks, applications, etc.) to detect unusual patterns or behaviors that might indicate a threat. For example, Splunk uses machine learning to analyze vast amounts of log data, correlating different real-time events to identify anomalies. It provides dashboards that visualize data to make threat patterns more apparent, allowing your SOC to quickly respond to emerging risks. Similarly, IBM QRadar employs advanced analytics and AI to prioritize alerts by severity, helping SOC analysts focus on the most critical threats. Microsoft Sentinel integrates with cloud platforms like Azure and third-party security tools, offering real-time threat intelligence and behavioral analytics, ensuring your team never misses an important event.
- EDR (Endpoint Detection and Response): EDR solutions like CrowdStrike Falcon, SentinelOne, and VMware Carbon Black are designed to continuously monitor endpoint activities (like processes, applications, and files) and detect suspicious behavior. CrowdStrike Falcon provides endpoint visibility and uses AI to detect attacks based on behavioral patterns, even those involving fileless malware or sophisticated lateral movements. SentinelOne goes a step further by offering autonomous detection and response, meaning that once a threat is detected, it can automatically contain and remediate the attack without waiting for human intervention. VMware Carbon Black excels at recording every endpoint action, creating a detailed timeline of events to allow your SOC to quickly trace and contain an attack. These tools help bridge the gap that traditional antivirus leaves open, as they can identify even the most subtle or emerging threats.
- NDR (Network Detection and Response): NDR tools like Cisco Stealthwatch, Darktrace, and Arista Awake provide real-time visibility into network traffic and detect malicious activities that may otherwise go unnoticed. Cisco Stealthwatch uses encrypted traffic analytics and advanced behavioral models to monitor traffic patterns across your network, spotting insider threats, lateral movement, and other complex attacks. By analyzing traffic, it can detect deviations from the norm, even when the data is encrypted. Darktrace takes a different approach, using AI to learn what’s ‘normal’ for your network and then automatically flags deviations that may indicate an attack. It specializes in identifying previously unknown threats and providing early warning before they cause damage. Arista Awake integrates machine learning with human expertise to detect threats that exploit specific network weaknesses, often missed by other tools.
Example: If you’re still relying on basic antivirus or legacy detection tools, you’re leaving significant gaps. Companies like Palo Alto Networks and Cisco offer advanced solutions that combine SIEM, EDR, and NDR capabilities to provide a multi-layered approach to threat detection. Palo Alto’s Cortex XDR platform integrates data from endpoints, networks, and cloud environments to detect attacks that cross different security layers. It uses AI to correlate data and uncover complex attack paths, such as multi-stage attacks that might evade more straightforward detection tools. Cisco’s SecureX platform unifies data from different detection tools and correlates it with real-time threat intelligence to give a clearer view of potential threats, speeding up detection and response.
Automated Threat Intelligence Feeds: One significant leap forward in threat detection is the use of automated threat intelligence feeds. Solutions like ThreatConnect or Recorded Future can automatically feed new and emerging threat data into your SIEM and EDR platforms. This enables real-time updates on the latest tactics, techniques, and procedures (TTPs) used by attackers worldwide. This ensures that your detection tools stay ahead of the curve, identifying zero-day attacks and new vulnerabilities before they are exploited.
By leveraging these advanced tools and capabilities, your SOC can detect threats faster and more accurately and respond before they cause significant damage. The combination of SIEM for logs and event correlation, EDR for endpoint visibility and response, and NDR for monitoring network traffic gives your SOC a holistic view of potential threats. Companies like Palo Alto Networks, Cisco, CrowdStrike, and Darktrace have led the charge in delivering these advanced detection solutions, allowing organizations to stay ahead of evolving threats.
Conclusion Part 1
A well-functioning SOC is your organization’s best defense against cyber threats. By focusing on these key areas—visibility, detection, automation, and response—you’ll ensure that your SOC operates like a well-oiled machine. Ensure you have the right tools, regularly refine your processes, and keep an eye on the latest security trends to stay ahead of attackers.
“A top-notch SOC isn’t just about the tools you use. It’s about how your technology and team work together to protect what matters most.”

