4 Key Steps to Stopping Ransomware Attacks
In this blog post, I’ll discuss the history of ransomware attacks, several of the older but more interesting variants, and most importantly, the key to stopping ransomware attacks in detail.
Let’s get started with what you probably already know, ransomware attacks are increasingly sophisticated, targeting vulnerabilities in systems, processes, and people. To effectively combat this growing threat, organizations must adopt a multi-layered strategy that addresses prevention, escalation, recovery, and security maturity. And let’s briefly introduce the 4 keys to stopping ransomware attacks at a very high level – we will provide the details in the last section.
- Prevention focuses on hardening systems against initial compromise. By training employees to recognize phishing attempts, implementing email scanning technologies, and keeping software up-to-date, businesses can reduce the likelihood of successful attacks.
- Escalation Defense aims to limit lateral movement within a compromised network. Attackers exploit system flaws to gain privileges and access high-value data, making robust security practices crucial for containment.
- Recovery and Resilience strategies, such as reliable backups, network segmentation, and content filtering, help organizations quickly recover while minimizing downtime and damage.
- Improved Security Controls and Maturity enhance baseline protections through advanced tools and network segmentation, ensuring long-term defense against ransomware threats.
How Significant is the Ransomware Problem?
In reviewing recent cybersecurity surveys, including the Verizon Data Breach Investigations Report (DBIR) and the Cybersecurity Insiders Survey, several key findings have emerged:
- Prevalence of Ransomware Attacks: A significant majority of organizations have encountered ransomware incidents, highlighting the pervasive nature of this threat.
- Rapid Growth: Ransomware damages surged from $325 million in 2015 to $20 billion in 2021, a 57-fold increase.
- Future Projections: Damages are expected to grow by 30% annually, reaching $265 billion by 2031, with attacks occurring every 2 seconds.
- Impact on Small Businesses: The Verizon DBIR indicates that 43% of all breaches affect small businesses, underscoring their vulnerability to cyber threats.
- Growing Concern Over Malware and Ransomware: Approximately 70% of organizations anticipate that malware and ransomware will pose a greater threat in the coming year.
- Likelihood of Future Attacks: 76% of respondents consider a malware attack within the next 12 months to be moderately to extremely likely.
- Perceived Threat Level: A combined 86% of survey participants view malware and ransomware as either an extreme (49%) or moderate (37%) threat.
- Primary Attack Vectors: Phishing emails are identified as the most dangerous attack vector by 54% of respondents, followed by trojans at 13%.
- Effectiveness of Endpoint Protection: Notably, 75% of companies infected with ransomware were operating up-to-date endpoint protection, suggesting that traditional defenses may be insufficient against evolving threats.
- Global Economic Risk: The World Economic Forum has ranked cyber threats as the fourth greatest risk to world economies, reflecting the widespread concern among security leaders.
- Sources of Attacks: The Verizon DBIR reports that approximately 70% of attacks originate from external actors, 30% from insiders, 39% from criminal groups, and 23% from state-affiliated entities.
- Initial Access: LockBit affiliates typically gain entry into target systems through methods such as phishing emails, exploiting unpatched vulnerabilities, or leveraging compromised Remote Desktop Protocol (RDP) credentials.
- Privilege Escalation: Once inside, the malware attempts to escalate privileges to gain administrative access, allowing it to disable security features and spread laterally across the network.
- Payload Deployment: The ransomware payload is deployed, often configured to execute automatically upon system startup.
- Data Encryption: LockBit employs a combination of Advanced Encryption Standard (AES) for file encryption and RSA for encrypting the AES key. This dual-layer encryption ensures that without the RSA private key, decrypting the files is virtually impossible.
- Ransom Note Delivery: After encryption, LockBit drops a ransom note in each affected directory, providing instructions for payment and decryption.
- Speed: LockBit is known for its rapid encryption process, minimizing the window for detection and response.
- Customization: The ransomware can be tailored to target specific file types and directories, increasing its effectiveness against particular organizations.
- Evasion Techniques: LockBit incorporates advanced anti-analysis and evasion strategies, such as disabling security tools and employing obfuscation methods to avoid detection.
- Social Engineering Training: Traditional, infrequent training sessions are insufficient. Instead, adopt dynamic training techniques like simulated phishing campaigns and real-time feedback to educate employees about recognizing malicious links and attachments. Reinforce verification protocols for emails containing unexpected attachments or links by requiring multi-channel confirmation.
- Email Content Scanning and Filtering: Leverage advanced email security tools capable of identifying and quarantining malicious attachments, URLs, and spoofed sender addresses. Incorporate AI-driven anomaly detection to recognize unknown threats and flag suspicious emails for manual review.
- Patch Management: Maintain a robust and automated patch management process to close vulnerabilities promptly. Attackers exploit known vulnerabilities in outdated software and operating systems, often within hours of a public disclosure. Use vulnerability scanners to identify missing patches and prioritize critical fixes based on severity and exposure risk.
- Privilege Escalation: Attackers exploit misconfigured permissions, outdated access controls, and unpatched software to elevate their privileges. They often leverage tools like Mimikatz to extract credentials or abuse Kerberos tickets for lateral movement.
- Network Reconnaissance: Before escalation, attackers scan the network for high-value targets, such as file servers, databases, or backup systems. Implement network monitoring solutions to detect and disrupt unusual lateral movements.
- Zero Trust Principles: Deploy Zero Trust architectures to restrict access to sensitive systems, requiring continuous authentication and verification for every user and device.
- Backup Solutions: Implement immutable and air-gapped backups to prevent attackers from encrypting or deleting them. Regularly test recovery processes to ensure data integrity.
- Network Segmentation: Divide the network into isolated segments using VLANs or microsegmentation. Ensure critical systems and sensitive data are accessible only to authenticated users with explicit permissions.
- Email Content Filtering and Sandboxing: Use sandboxing solutions to execute and analyze attachments in a controlled environment before they reach the user, mitigating the risk of zero-day malware.
- Continuous Training: Reinforce social engineering training with regular updates and practical simulations to adapt to evolving attacker techniques.
- Security Controls: Deploy layered security solutions, including endpoint detection and response (EDR), intrusion prevention systems (IPS), and behavior analytics to detect and block threats in real-time. Regularly assess and update your security policies to match the threat landscape.
- Network Segmentation: Employ advanced segmentation techniques to isolate sensitive environments, such as production databases, from general-purpose systems. Use firewalls and access control lists (ACLs) to enforce strict traffic policies and limit potential attack vectors.
- Comprehensive Evaluation: Analysis of processes, endpoint and email security, network defenses, and data protection.
- Expert Analysis: Insights from seasoned cybersecurity professionals.
Additional Ransomware threat related areas we evaluate as a part of this assessment:
- Remote Access protocols including RDP/RDGateway, VPN
- Remote Management/Monitoring Software
- Phishing susceptibility
- External services including file sharing Protocols (SMB)
- Browser-based vulnerabilities
- Operating system hardening level
- Adversary lateral-movement susceptibility
- Actionable Insights: Reports with tailored recommendations and prioritized action plans.
- Peace of Mind: Clear understanding of vulnerabilities and steps to mitigate them.
- Pre-Assessment: Information gathering and scheduling.
- Remote Session: Detailed assessment of security domains and collaborative discussions.
- Reporting: Delivery of a comprehensive report with findings, scores, and recommendations.
- Enhanced security posture and minimized risks.
- Regulatory compliance and due diligence.
- Business continuity and customer trust protection.
- Proven cybersecurity expertise.
- Custom-tailored solutions.
- A client-first approach ensuring optimal outcomes.
These findings underscore the critical need for organizations to enhance their cybersecurity measures, particularly in the face of sophisticated ransomware attacks.
Exploring the Ransomware Problem
Ransomware attacks have escalated significantly, with global damages projected to reach $42 billion by the end of 2024, a substantial increase from previous years. The average cost of a ransomware attack has also risen sharply, with recovery expenses now averaging approximately $1.85 million per incident.
This surge is attributed to the emergence of financially motivated, non-state attackers who increasingly target vulnerable entities such as municipalities, educational institutions, and healthcare organizations. These sectors often lack robust cybersecurity defenses, making them attractive targets for cybercriminals. The shift in attacker focus underscores the critical need for enhanced cybersecurity measures across all organizational levels to mitigate the growing threat of ransomware.
Along with the common non-tech criminal getting involved in the ransomware attack game, the rise in attacks can also be attributed to the dramatic increase in rentable malware droppers like Emotet. These droppers can be essentially hired to deliver malware of virtually any kind to targeted systems. Moreover, there has been a significant rise in black-market Software-as-a-Service networks with actual helplines for the non-technical attacker or “script kiddies” to get guidance from seasoned cyber-criminal organizations launch attacks.
How Does Ransomware Infiltrate and Lock My System and Data
In general, ransomware is a malware variant that encrypts critical data on a victim’s system using asymmetric or symmetric cryptographic algorithms. Upon execution, it targets specified file types or directories, generating a unique encryption key for the session.
The malware often replaces original files with encrypted versions and removes shadow copies to prevent recovery. Attackers store the private decryption key on a remote command-and-control server, making local recovery infeasible without their assistance. Victims are presented with a ransom demand, typically requiring cryptocurrency payment, to obtain the decryption key necessary to restore access to their data.
The malware is most often delivered through phishing emails and, now, more commonly spear phishing emails; the ransomware locks hard drives or other parts of the system, making data assets virtually impossible to access.
While there are countless types of ransomware, and new families of malware have far surpassed the following, 4 families of the malware have not only done a significant amount of the early and total damage, but also provide interesting insights into how the malware and attacks work: Dharma, Ryuk, GandCrab and of course LockBit.
Dharma Ransomware
Dharma ransomware first emerged in 2016 as variant of the Crysis ransomware and became one of the most potent forms of ransomware in its own right. The authors of Dharma at one point were releasing new updates for the malware which prevent standard decryption products from being created. What made Dharma so successful is that it spreads by targeting internet-facing ports and remote desktops.
As opposed to most ransomware attacks that leverage phishing attacks, Dharma can gain access to networks without even having to get a victim to click a link or download a malicious file from a phishing email. The malware is manually delivered by attackers who exploit Remote Desktop Protocol (RDP) services via TCP port 3389 and brute force the password to gain access to a computer.
Phobos, another devastating piece of ransomware is similar to Dharma in that it can arrive on systems in a variety of ways. It can infiltrate systems via open or insecure remote desktop protocol (RDP) connections on port 3389, brute-forced RDP credentials. Phobos operators can also leverage malicious attachments, downloads, patch exploits, and software vulnerabilities to gain access to an organization’s endpoints and network.
Ryuk Ransomware
Ryuk ransomware is more lucrative than its predecessor Hermes. It targets large organizations and government agencies that end up paying up in large amounts. In fact, without the big payoffs, executing Ryuk attacks is not sustainable. Attacks using Ryuk involve a high degree of manual processes including direct exploitation and payment requests handled via email. Attackers won’t want to waste their time if they don’t believe they are targeting a lucrative target.
The ransomware was initially attributed to North Korea, but now researchers believe that it’s more likely to be the Russian-based organized crime group called Grim Spider which created the most devastating strain of the malware a year ago. It is estimated that Ryuk earned it’s the Russians more than $3.7 million in its first four months.
There have been a variety of high-profile attacks that put Ryuk in the spotlight several years ago including Lake City, Florida paid $530,000 in bitcoin to cybercriminals to unlock its data in June and fired its IT manager for not protecting the organizations from the attacks. It followed an attack on another Florida city, Riviera Beach, which paid $600,000 to unlock encrypted files.
GandCrab Ransomware
GandCrab ransomware first emerged several years ago and wreaked havoc for the next 12 months. Described by Europol at the time as “one of the most aggressive forms of ransomware”, GandCrab was on an affiliate model, its authors leased out the ransomware in exchange for a portion of the profits.
GandCrab is distributed via multiple spreading vectors, which include spam emails, exploit kits and other affiliated malware campaigns. GrandSoft and RIG are the two most commonly used exploit kits for distributing GandCrab along with the high number of malicious spam emails that the ransomware leverages. These spam emails trick users into opening the file contained inside the attached ZIP archive, which is generally a script that downloads the GandCrab ransomware and executes it.
Like Dharma, when free decryption tools were released to combat GandCrab its developers released new versions. The group behind GandCrab suggested that they earned over $2 billion but have now ceased operations suggesting their first of its kind ransomware-as-a-service model has made them comfortable.
A decryption tool for the most recent version of GandCrab is available from the awesome group No More Ransom.
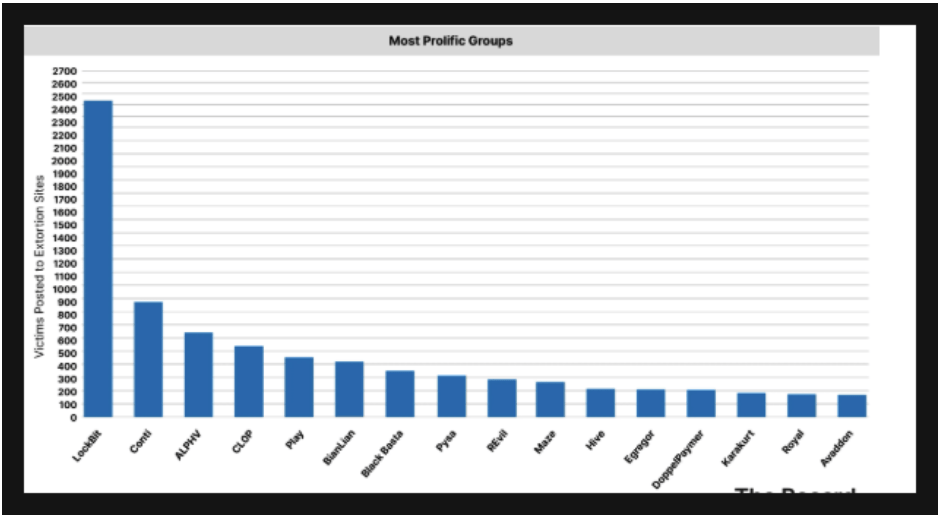
LockBit – The Mother of All Ransomware Attacks
In May 2024, the U.S. Department of Justice unsealed charges against Dmitry Yuryevich Khoroshev, a Russian national, identifying him as the creator, developer, and administrator of the LockBit ransomware group.
LockBit has been one of the most prolific ransomware operations responsible for numerous attacks worldwide. The indictment marked a significant step in international efforts to combat ransomware activities.
LockBit stands out as one of the most damaging ransomware families, responsible for a significant number of attacks globally.
Execution and Data Encryption Process:
Notable Characteristics:
The 4-Step Solution to Protecting Against Ransomware Attacks
Because IT security, incident response and cybersecurity organizations in general have investigated so many ransomware attacks over the past several years, we are all getting a sense of how to defend more effectively. That said, the team at Lodestone has taken cyber-defense a step further than simply having a “sense” of how to defend. They have leveraged their deep understanding of how ransomware infiltrates a system, spreads throughout a network and uses locks data and system functions to attack.
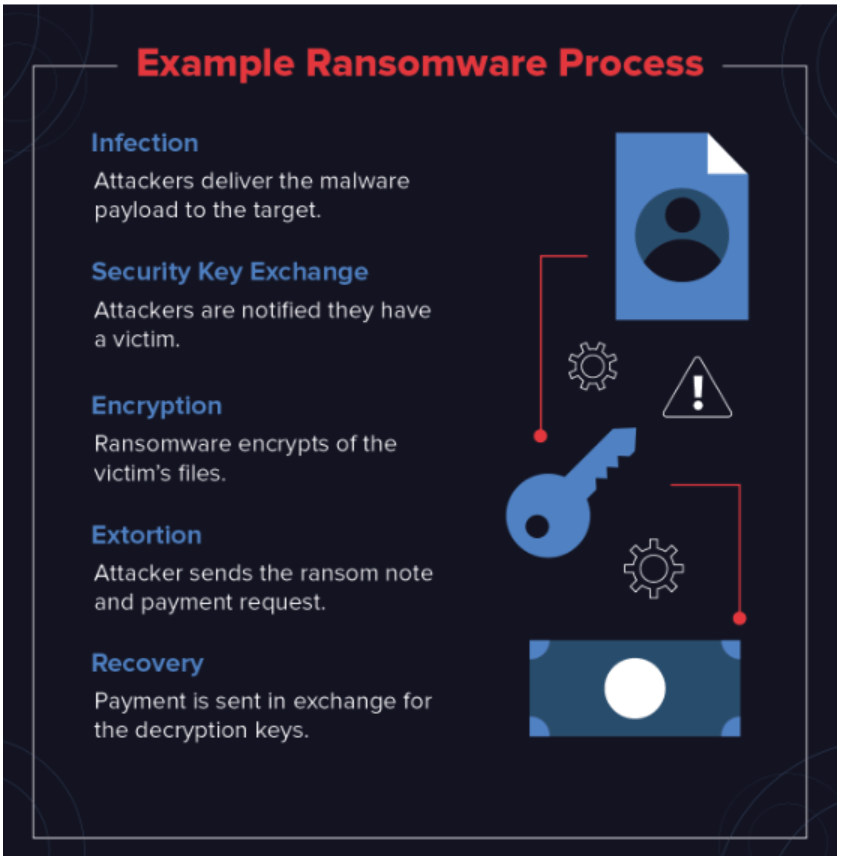
Image from Varonis – https://www.varonis.com/blog/how-to-prevent-ransomware/
Detailing the 4 Steps Organizations Should Take to Defend Against Ransomware Attacks
In cybersecurity we often refer to an attack as having “Land and Expand” strategy. Meaning the cyber-criminal must figure out how to get the malware onto the system. After they “Land” the attacker must move the malware to other systems by escalating credentials or some other means to “Expand” their attack and find the most lucrative victims.
To prevent an escalation of the attack or lateral movement of the malware from one system to another you must first take your system off the network. You don’t necessarily need to shut down the system however it should be isolated.
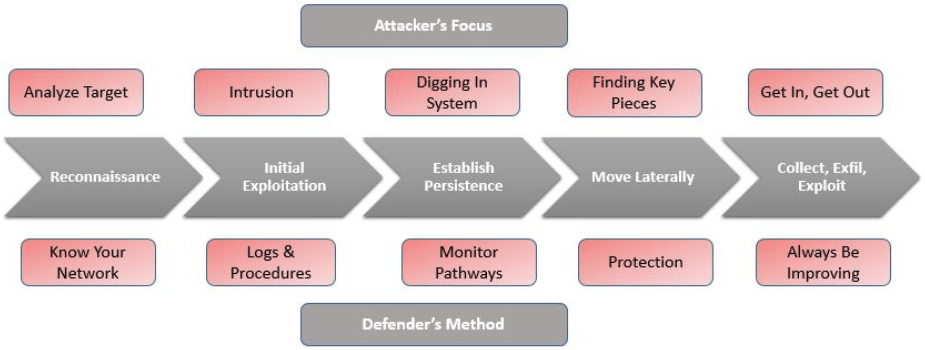
https://www.graylog.org/post/cyber-security-understanding-the-5-phases-of-intrusion
Finally, Local and domain administrative accounts – with access to the organization’s systems and data – are powerful tools in a network. Their use should be tightly controlled and locked down as should any systems that contain PII or the personal information of employees, customers and partners.
Also, administrators should use separate accounts; one for day-to-day business use including web browsing and emails and a privileged administrator account that should only be used on separate administration devices. This reduces the risk of an infected device being used for admin purposes.
Ultimately, administrator accounts should be prevented from browsing the web and accessing emails and only be used when a task requires elevated permissions. The principle of ‘least privilege’ (where accounts and users have the minimum amount of access needed to perform their role) should be implemented wherever possible.
Let’s walk through how to execute the 4 steps and how they can help close the gaps that cyber-criminals use to steal billions from their victims.
Prevention
The goal of prevention is to fortify systems and reduce the likelihood of a successful attack. This involves hardening targets against common attack vectors such as phishing, Remote Desktop Protocol (RDP)/Remote Access attacks, and other vulnerabilities through a multi-pronged approach:
Escalation
Ransomware attacks often exploit lateral movement to expand their reach within a compromised environment. After initial access, attackers use privilege escalation to gain control over critical systems:
Recovery and Resilience
Resilience focuses on minimizing the impact of an attack and ensuring business continuity:
Improved Security Controls and Maturity
Enhancing the maturity of your security controls ensures robust and adaptable defenses against evolving threats:
This enhanced approach integrates technical rigor with operational resilience, ensuring a proactive and responsive defense against ransomware threats.
Conclusion & Solution – Falcon Guard’s Ransomware Preparedness Assessment
Our proprietary Ransomware Preparedness Assessment offers a comprehensive evaluation of your organization’s ability to prevent, detect, and respond to ransomware threats. Leveraging industry best practices and deep cybersecurity expertise, we help you identify vulnerabilities and fortify your defenses.
Falcon Guard’s Innovative Ransomware Preparedness Assessment
Service Overview:
FalconGuard’s Ransomware Preparedness Assessment evaluates your organization’s readiness to prevent, detect, and respond to ransomware threats using industry best practices and cybersecurity expertise.
Key Features:
Three-Step Process:
Business Benefits:
Why FalconGuard?
To learn more about how Falcon Guard can assist with deciding on optimal cybersecurity solutions for your organization, or if you suspect that you have been targeted by an attack, contact us at (858) 349-2610 or fill out our Contact Us form on our website.

